Metasploit Offers Exploits For The Mac Os X Operating System
- Metasploit Offers Exploits For The Mac Os X Operating System Download
- Metasploit Offers Exploits For The Mac Os X Operating System Download
A macOS developer has discovered an exploit that can bypass the operating system's file privacy and security protections.
Internet Explorer (formerly Microsoft Internet Explorer and Windows Internet Explorer, commonly abbreviated IE or MSIE) is a series of graphical web browsers developed by Microsoft and included in the Microsoft Windows line of operating systems, starting in 1995.It was first released as part of the add-on package Plus! For Windows 95 that year. Later versions were available as free downloads. Msrpc exploit. Msrpc exploit. For each attack, the course explains the vulnerability, how various tools exploit it, the signature of the attack, and how to harden the system or application against the attack. Students who sign an ethics and release form are issued a USB drive containing the attack tools examined in class.
If you know the victim machine’s operating system and version, you can specify the target for the exploit. Some modules provide an automatic targeting option. If you are unsure of the operating system or version, you can use the automatic targeting option if it is available, to automatically detect the victim machine’s OS and version. Vulnerability Management On-Premises. Metasploit System Requirements and Documentation. OPERATING SYSTEMS.
May 21, 2019 Heroes of Might and Magic III is one of (if not) the best fantastic/medieval strategy game for Mac and PC featuring orchestral soundtracks and marvellous soothing animated graphics. This third release is probably also the best in all the 3DO related releases from mid 1990’s to mid 2000’s. Installing the Heroes of Might and Magic 3: HD+ Mod Click Install Softwarefollowed by Choose Setup Executableagain. Select the HD+ Mod installation file and follow and on-screen instructions. When prompted, select to launch Heroes 3 HD (after the installation has been completed). Heroes of Might and Magic III is one of (if not) the best fantastic/medieval strategy game for Mac and PC featuring orchestral soundtracks and marvellous soothing animated graphics. This third release is probably also the best in all the 3DO related releases from mid 1990's to mid 2000's. Heroes of might and magic 3 for mac os x. Welcome to the Heroes of Might and Magic 3 page. This page contains information + tools how to port Heroes of Might & Magic 3 in a few simple steps (that even a noob can understand) so you can play it on your Mac just like a normal application using Crossover.So if you haven’t Crossover yet, then sign up here and buy the program or if you want to test it first, for the 14 days trial.
The exploit, created by developer Jeff Johnson, impacts the 'Transparency, Consent, and Control' (TCC) framework that was introduced in macOS Mojave. Johnson also tested the exploit in macOS Catalina and the first macOS Big Sur beta.
Essentially, the TCC framework restricts the ability for apps in macOS to access certain protected files or folders. As an example, Johnson writes that an app may not have access to the ~/Library/Safari folder unless it is explicitly granted.
In a blog post disclosing the exploit, Johnson said that there are two fatal flaws to the protections — exceptions are based on a bundle identifier instead of a file path, and the system only 'superficially' checks an app's code signature.
'Thus, an attacker can make a copy of an app at a different location on disk, modify the resources of the copy, and the copy of the app with modified resources will still have the same file access as the original app, in this case, Safari,' Johnson wrote.
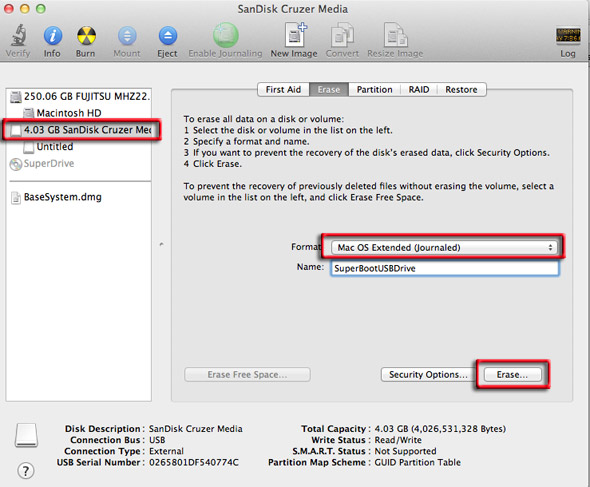 Create Your Own Mac Recovery HD on Any Drive Apple also created a utility called OS X Recovery Disk Assistant that can create a copy of the Recovery HD on any bootable external drive you have connected to your Mac. This is good news for the many Mac users who would like to have the Recovery HD volume on a drive other than the startup volume.
Create Your Own Mac Recovery HD on Any Drive Apple also created a utility called OS X Recovery Disk Assistant that can create a copy of the Recovery HD on any bootable external drive you have connected to your Mac. This is good news for the many Mac users who would like to have the Recovery HD volume on a drive other than the startup volume.
A proof-of-concept attack created by the developer uses a flaw in Safari to leverage those vulnerabilities. It involves a modified version of Safari which can access protected files and send off private data to a server. The second app is the one that actually downloads and launches the modified Safari — a task that any app downloaded from the web can accomplish.
Because of the exploit, Johnson claims that the Mac's privacy protections are 'mainly security theater and only harm legitimate Mac developers allowing apps to bypass them through many existing holes.'
The developer first disclosed the bug to the Apple Security Bounty program in December 2019, sparking several months of back-and-forth updates. Although Apple Product Security told Johnson they'd fix the issue in spring 2020, he said that it's still present in the macOS 11 Big Sur beta.
Importantly, the exploit only really impacts the privacy protections built into macOS Mojave and later. In other words, it takes macOS security back to High Sierra and earlier.
Because of that, Johnson writes that the level of concern over the vulnerability really depends on 'how you feel in general about macOS privacy protections.'
Metasploit Offers Exploits For The Mac Os X Operating System Download
The exploit can be leveraged by non-sandboxed malicious apps on a Mac, so the best mitigation strategy would be to exercise caution when downloading any app not from the Mac App Store.
Metasploit Offers Exploits For The Mac Os X Operating System Download
AppleInsider has affiliate partnerships and may earn commission on products purchased through affiliate links. These partnerships do not influence our editorial content.